Cloud Computing - IaaS, PaaS and SaaS
This article is second part of three part series of cloud computing. In this series, I will cover the following topics
- What is cloud computing?
- Types of cloud computing?
- Different types of cloud service models (IaaS, PaaS and SaaS) - this post
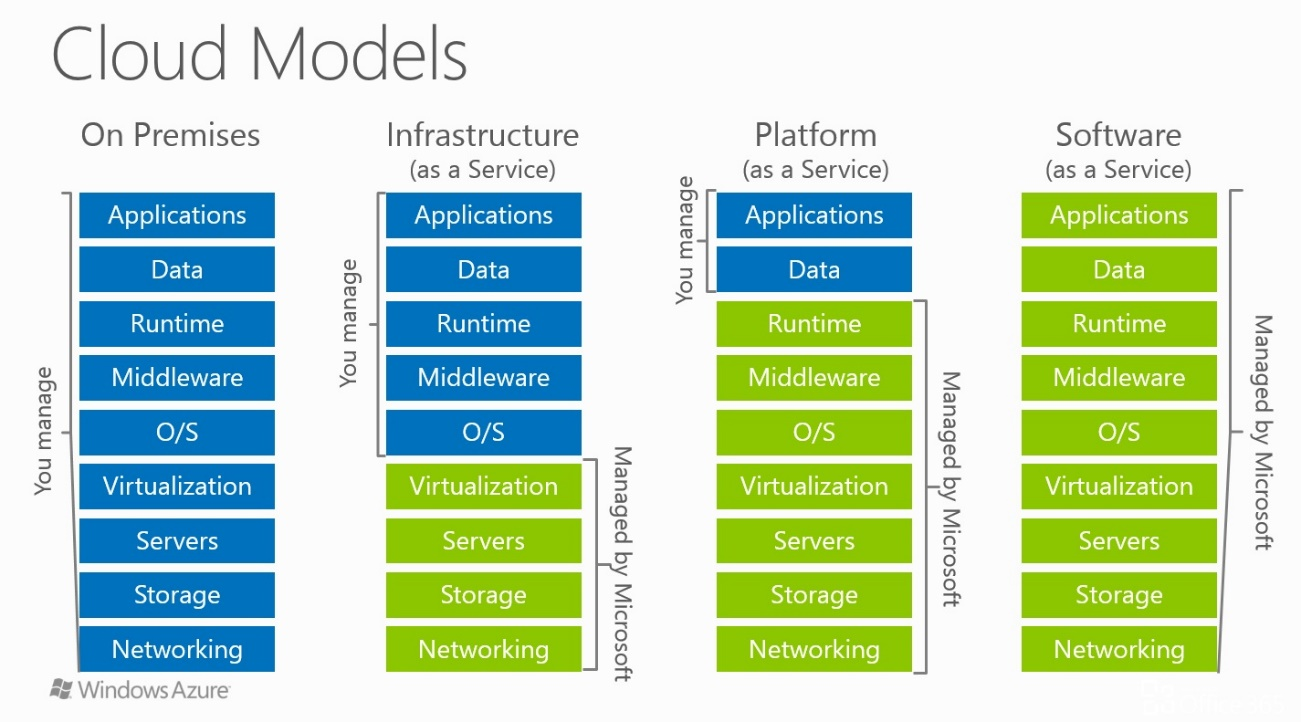
IaaS, PaaS, and SaaS are the main models of providing cloud services.
- IaaS — a client gets only infrastructure. In this model, azure instantly provides servers, storage, networking and virtualisation.
- PaaS — a client gets infrastructure and software for application development. In this model, azure provides platform to host and deploy your applications. It allows the developers to focus on the development, testing and deployment of apps faster. Examples: Azure App Service, Azure Kubernetes Service (AKS)
- SaaS — a client gets a ready-to-use application in the cloud. In this model, customer pays for ready to use software solutions like MS Dynamics 365, Salesforce etc.
Serverless is another popular model to host your applications. In this model, infrastructure is provisioned on demand automatically by Azure. Example: Azure Functions, Azure Container Instance (ACI)
It is important to discuss about security as many people misunderstand that by provisioning the resource, Azure or AWS will manage the security of your resources. Although some security protections are built into services, resource security will always remain as customer's responsibility.
By moving from on-premise data centre to cloud based service, you will be shifting major responsibilities to cloud service provider like Azure but as I said, it will always remain as customer's responsibility.
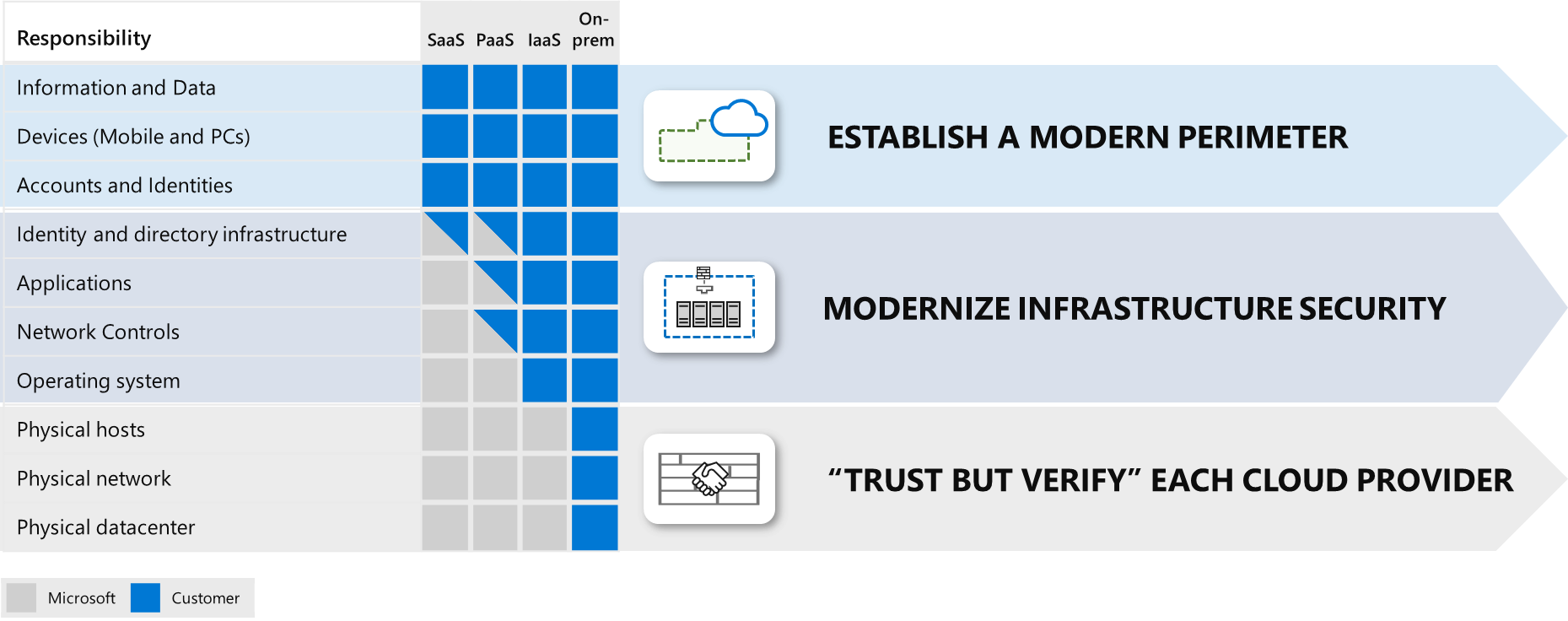
Azure documentation shares three key strategies to address shared responsibility as shown in the picture above
- Establish a Modern Perimeter – for the elements that your organization controls to ensure you have a consistent set of controls (a perimeter) between those assets and the threats to them.
- Modernize Infrastructure Security – for operating systems and middleware elements that are required by legacy applications; take advantage of cloud technology to reduce security risk to the organization.
- “Trust but Verify” each cloud provider – for the elements, which are under the control of the cloud provider. You should ensure the security practices and regulatory compliance of each cloud provider (large and small) meet your requirements.
References
- https://azure.microsoft.com/en-us/overview/what-is-azure/iaas/
- https://azure.microsoft.com/en-in/overview/what-is-paas/
- https://azure.microsoft.com/en-in/overview/what-is-saas/
- https://azure.microsoft.com/en-in/overview/serverless-computing/
- https://docs.microsoft.com/en-us/azure/architecture/framework/security/role-of-security